Insecure Active Directory Lab For Training (IaC)
TLDR; Vulnerable-AD-Lab is an AD environment developed to practice AD security. The idea of this IaC project is to build a functional Vulnerable Active Directory Lab from scratch without using VM templates.This IaC project integrates WazeHell’s vulnerable-AD script: https://github.com/WazeHell/vulnerable-AD. The final product of this automation script is a Windows 2019 server with a misconfigured AD service and a Windows 10 workstation connected to the same domain.
The lab includes different misconfigurations, such as misconfigured ACLs/ACEs, Object Descriptions, groups, and services. It also uses common insecure policies and configurations allowing attacks like Kerberoasting, AS-REP Roasting, Silver Ticket, Golden Ticket, Pass-the-Ticket, and DCSync attacks.
The main objectives of this environment are to be an asset for security professionals to examine their tools and skills, help system administrators better understand the processes of securing AD networks and help teachers/students to teach/learn Active Directory security in a safe and prepared environment.
How to build the environment?
Assumptions
I assume you already have a cloud environment or a local virtual environment and there is a DHCP server running in the network. If that’s not the case, check out the first post of the Applied Purple Teaming Series. In that post, I show how to setup a Virtual Environment using EXSi: Applied Purple Teaming Series - Part 1.
Download Windows ISOs
- https://www.microsoft.com/en-us/evalcenter/download-windows-server-2019 (DC)
- https://www.microsoft.com/en-us/evalcenter/download-windows-10-enterprise (Client)
Copy the path of each ISO and replace the value of os_iso_path and dc-os_iso_path in credentials.json. If you are deploying it on a VBox hypervisor, make sure that you also add the md5 checksum for each ISO ( Refer to the given example ).
Install Packer
- https://www.packer.io/
sudo apt-get -y update sudo apt-get -y install packer
Currently, the project supports vSphere and VirtualBox. If you will deploy the environment using vSphere, download vsphere-iso since Packer doesn’t automatically download it by default like when VirtualBox-iso is used.
wget https://github.com/jetbrains-infra/packer-builder-vsphere/releases/download/v2.3/packer-builder-vsphere-iso.linux
mv packer-builder-vsphere-iso.linux packer-builder-vsphere-iso
Before deploying the environment, make sure there is a DHCP server running and the VMs can access the internet. This is needed becasue Packer will need to connect to install the lab scripts. Create your own credentials.json file using the provided example.
Send it
After configuring environment variables, build the AD server using the following command:
packer build -var-file=./credentials.json windows19/windows2019.json
The AD needs to download AD-Domain-Services Windows Feature and then install the AD so it might take around 10 minutes to finish the deployment of the first VM.
When done, execute the following command so that the client VM can look up the domain name successfully.
DC_FOLDER="windows19/"
CLIENT_10="windows10/"
DC_IP=$(grep 'IPv4.*Address.*' $DC_FOLDER/pulled/ipconfig.out | cut -d':' -f2 | cut -d'(' -f1 | sed -e 's/ */ /g' -e 's/^ *\(.*\) *$/\1/')
sed 's/1.1.1.1/'$DC_IP'/' $CLIENT_10/base/join-ad.ps1 > $CLIENT_10/setup/join-ad.ps1
Finally, build the other workstation vm.
packer build -var-file=./credentials.json windows10/windows10.json
To confirm that the workstation is joined, go to Active Directory Users and Computers > Computers and you should find the workstation added to the domain as shown below:
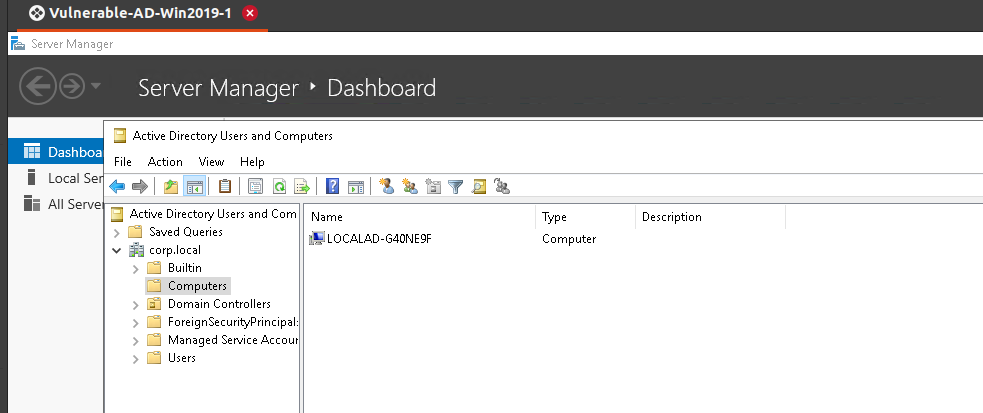
Putting everything together
echo "Installing prerequisites"
sudo apt-get -y update
sudo apt-get -y install packer
echo "Setting up folder variables"
DC_FOLDER="windows19/"
CLIENT_10="windows10/"
mkdir -p $DC_FOLDER/pulled
echo "Build DC01"
packer build -var-file=./credentials.json windows19/windows2019.json
# To change the DNS settings
echo "Extracting the DC's IP Address"
DC_IP=$(grep 'IPv4.*Address.*' $DC_FOLDER/pulled/ipconfig.out | cut -d':' -f2 | cut -d'(' -f1 | sed -e 's/ */ /g' -e 's/^ *\(.*\) *$/\1/')
echo "DC IP: " $DC_IP
echo "Preparing the AD join scripts"
# Change join-ad.ps1 according to the given DHCP lease.
sed 's/1.1.1.1/'$DC_IP'/' $CLIENT_10/base/join-ad.ps1 > $CLIENT_10/setup/join-ad.ps1
echo "Build Client VM"
packer build -var-file=./credentials.json windows10/windows10.json
echo "Done! happy hacking : )"
Why don’t you use Detection Lab?
Detection Lab is a great project that can also be used to practice network and system security. I think Detection Lab is the go-to environment for many, including me. It gives security practitioners good visibility. I think it could help in many ways, and I personally have used it along with security onion solutions to observe the artifacts of some attack techniques. However, last week I had a different goal. I was working on an offensive security automation tool. I wanted a relatively light and rebuildable environment that could be deployed on my ESXi server to quickly be able to test the tool I was developing. This is how this lab was born.
While working on this project, I tried not to use many automation technologies. If you read the source code, you will notice that I can improve things like the time wait between the tasks and probability use other automation technologies like Ansible and maybe deploy some of the settings faster, but I didn’t. The reason is that I didn’t want to make it complicated for beginners. I noticed that this is the first main problem non-DevOps folks face when they try to use these kinds of projects, so I avoided it by only using one automation technology.
Coming full circle, this IaC should be easy to deploy by teachers, students, security practitioners, and system administrators, allowing practitioners to examine their tools and skills, help system administrators better understand the processes of securing AD networks, and should help teachers/students to teach/learn Active Directory security in a safe and prepared environment.
Date: 06-12-2022
You can find Vulnerable-AD-Lab repository here